The Breach Notification System in China
——From the Perspective of Discretion Regulation
Tang Lin,Yang Li(a.Koguan School of Law,.China Institute for Smart Court, Shanghai Jiao Tong University,Shanghai 200030,China)
Abstract: Article 57 of the Personal Information Protection Law of the People's Republic of China establishes the breach notification system for the first time, which largely derives from the General Data Protection Regulation(GDPR). The discussion on how to regulate the discretion of processors and build a coordinated mechanism between regulatory authorities and regulated entities has raised public concern. In particular, proper regulation for"discretion" is the key to the effective operation of the breach notification system. By drawing reference from"structuring discretion",this paper analyzes the theoretical framework of reputation sanctions and third-party enforcement strategy. It proposes to focus on the regular supervision of discretion, weakening clear regulatory indicators,and the effectiveness of notification content in terms of the improvement of the breach notification system.
Keywords:breach notification;third-party enforcement;discretion;personal information protection
1 Introduction
On August 20, 2021, the Standing Committee of the National People's Congress issuedthe Personal Information Protection Law(hereinafter referred to as "PIPL"), in which Article 57 establishes, for the first time, the breach notification system in China, clarifying the obligation of personal information processors to notify the relevant authorities and affected individuals after the occurrence of an information breach①Article 57 of PIPL: (1) Where leakage, tampering or loss of personal information occurs or may occur, a personal information processor shall immediately take remedial measures, and notify the authority performing personal information protection functions and the relevant individuals. The notice shall include the following matters: (a) The categories of personal information that is or may be leaked, tampered with or lost, and the causes and possible harm of the leakage, tampering or loss of the personal information; (b)Remedial measures taken by the personal information processor and measures the individuals can take to mitigate the harm; (c) The contact information of the personal information processor. (2) Where the measures taken by the personal information processor can effectively avoid the harm caused by information leakage,tampering or loss,the personal information processor is not required to notify individuals; and where the authority performing personal information protection functions considers that harm may be caused, it shall have the right to require the personal information processor to notify individuals.. It is not a stretch to emphasize that, to a large extent, Article 57 of PIPL emulates Article 33 and Article 34 ofthe General Data Protection Regulation(GDPR). Essentially, the primary purpose of the breach notification system is to protect citizens from the ongoing harm that the personal information breach, including may cause but not limited to identity theft or fraud, financial loss, social disadvantages, and other adverse effects in social life②General Data Protection Regulation,Recital 85.. The EU's breach notification system was first established inthe E-Privacy Directive, which the GDPR later replaced. Articles 33 and 34 of GDPR provide for breach notification to the supervisory authority and subjects of personal information,respectively.At the supervisory authority level, the controller of personal data shall report the breach to the supervisory authority when it becomes aware of the violation (within 72 hours at the latest); at the personal information subject level, the personal information controller shall promptly notify the individuals when the breach is likely to pose a high risk to the rights and freedoms of natural persons. However, there are two significant challenges in the breach notification system in both the breach notification systems in PIPL and GDPR: firstly, how to regulate the discretion of notification delegated to personal information processors or controllers to encourage them to notify the affected individuals; secondly, how to break the regulatory capture in the course of long-term supervision, which would result in "paper compliance"for personal information processors.
1.1 The Paradox between Discretion and Reputational Sanction
The breach notification system incentivizes the relevant industries to govern and invest in protecting personal information primarily by dealing a reputation strikes and lowering social ratings for those involved in personal processing information. The effectiveness of reputational sanctions lies in the fact that both individuals and organizations are, to a greater extent, subject to the social impact of the disclosure of their prior behaviors[1]. On the one hand, in today's highly developed society of financial capital, especially for listed companies, the damage to their reputation caused by the exposure of information leaks may bring severe setbacks to their share prices③China Finance, Yuan Tong Express shares fall 1.71% after being interviewed for leaking 400,000 pieces of personal information,http://finance.china.com.cn/stock/ssgs/20201126/5440347.shtml,last accessed 2022/05/14.and the rapid loss of a large number of existing and potential customers④BBC News, Cathay Pacific data hack hits 9.4 million passenger, https://www.bbc.com/news/business-45974020, last accessed 2022/02/01.. On the other hand, information compromises in crucial industry sectors can even jeopardize national security and affect social stability and development[2].
Article 57(2) of PIPL entitles personal information processors to the discretionary power not to comply with the notification based on "effectively avoiding the harm". Similarly, Article 34(3)(b) of GDPR stipulates that if measures taken by personal information controllers ensure "the high risk to the rights and freedoms of data subjects …is no longer likely to materialize", the communication or breach notification could not be required. For companies,compliance with breach notification implies financial losses, potential commercial litigation, and strict government scrutiny. As a result, companies with the discretionary power prefer to "digest" breach events internally in anticipation of the enormous potential business risks and social responsibilities, and the breaches themselves often involve a spectrum of organizations, making it difficult to trace the source of the information breach[3]. Put another way, the theoretical assumption of reputation sanctions is that companies are economically rational and seek to maximize profits and need to calculate the costs and benefits between the investment in information security construction and the economic loss caused by breach notification[4]. Therefore, the more significant the negative impact of reputational sanctions, the greater the investment in information security needs to be correspondingly enhanced. However, the insanity and short-sightedness of the decision-makers and managers behind companies in their quest for economic profit often subvert the assumptions of rational economic man. A social survey on environmental protection in companies showed that the heads of compliance departments in over 200 companies had no idea of the specific penalties they would face for ecological pollution, relying overwhelmingly on rough estimates and everyday experience[5].
1.2 The Dilemma of Discretion Regulation
In addition, when making the decision not to notify affected individuals after being aware of a personal information breach, personal information processors will undoubtedly develop a series of processing institutions within their organizations to legitimize the requirement of Article 57(2) of PIPL that "measures … can effectively avoid the harm caused by information leakage, tampering or loss", to cope with the ex-post-facto supervision by the administrative authorities. Although both Article 57(2) of PIPL and Article 34(4) of GDPR also grant the administration the final judgment on the discretion of personal information processors, the reality is that individual information processors often control the large-scale information storage infrastructure, the actual operation, and maintenance of the network platform, which involves the whole life process of private information collection, storage, transmission, use, and destruction[6]. Individual information processors are in a position of the absolute monopoly of knowledge and information compared to administrative authorities. On the one hand, personal information processors represented by Internet enterprises take advantage of information asymmetry to meet administrative supervision most easily and cheaply to achieve "paper compliance". The external compliance adjustments regulated ones make seem to prioritize personal information protection issues. Still, they do little to change their internal workings without establishing a compliance culture reinforced by adequate training and controls[7].On the other hand, due to the decisive influence of the Internet giants, the administrative authorities often have been "captured" using identifying the explicit regulatory indicators in the process of long-term interaction with personal information processors[8],which are then absorbed as routine information into the daily compliance process of enterprises, ultimately resulting in a superficial and formalized supervision.
This paper intends to discuss the improvement of the breach notification system in terms of discretion-triggering criteria and supervision mechanism.
2 Breach Notification as Third-Party Enforcement Strategy
Reputational sanction usually refers to the behavior of public authorities, including administrative organs and judicial organs, through information disclosure in exercising their functions, exposing the negative information of the concerned parties, thereby affecting their external reputation and social evaluation. Under the auspices of solid information infrastructures, the current reputation sanction system in China can defend, among others, citizens'right to information and right to life and health quickly and efficiently in the fields of food and drug safety and environmental protection through the powerful means such as negative information records and negative labels to deal a severe reputation blow to corporate violations. In personal information protection, the breach notification system uses reputation sanctions to stimulate the industry to invest and pay attention to information security. Unlike traditional areas, Article 57 of PIPL imposes a mandatory third-party obligation on personal information processors and provides a certain amount of discretionary space for exemptions from breach notification, making them the "gatekeepers" under the framework of the unique information protection system.
2.1 Corporate Reputation Sanction System in Traditional Fields
Currently, China has established a trinity reputation sanction system for enterprises' illegal behaviors based on regular disclosure on government websites, credit file collection, and negative labeling of enterprise's past performance. On the one hand, administrative agencies are required to actively disclose administrative penalties and other related information according tothe Law of the People's Republic of China on Administrative Penalty,Open Government Information Regulation of the People's Republic of China,andInterim Regulation on Enterprise Information Disclosure; on the other hand, a complete enterprise credit file database is formed through the enterprise credit information disclosure system, credit files in the industry and the national public credit information platform, strengthening the reputation sanction using negative labels such as "List of Enterprises with Abnormal Operations", "List of Enterprises with Serious Illegal and Dishonest Act" and "Joint Punishment of Dishonesty Object List".
In essence, it is the key to understanding the mechanism of reputation sanction that the negative evaluations made by administration agencies widely disseminate as reputation information of enterprises to the relevant markets and society through the established social credit information platform. Corporate reputation information, which is built on top of the corporate information disclosure and social credit information system, directly reflects the compliance risk and operational status of enterprises, facilitating the flow of information in the market and the public's expectations regarding the stability of transactions[9]. Nevertheless, the shortcoming of a corporate reputation sanction system is that the effect of reputation sanction may be too heavy. Negative labeling, for example, can directly serve as a basis for other administrative activities, i.e., as long as an enterprise is included in any lists of negative labeling, all relevant government departments sharing the credit information platform will correspondingly take somewhat restrictive measures against it without any discretion.
2.2 The Legitimacy of Reputation Sanction by Third-Party Enforceme nt
The breach notification system in PIPL and GDPR intends to achieve reputation sanctions against personal information processors or controllers by compulsively notifying administrative agencies and affected individuals. From the perspective of PIPL, such a notification obligation is a public law liability, i.e., the personal information processors,as a private entity, participate in the enforcement process by performing the notification obligation. In other words,such a "gatekeeper liability" under public law is imposed on private parties because they can frustrating misconduct by withholding their cooperation from wrongdoers[10].
According to the gatekeeper theory, there are mainly three evaluative criteria to bear on gatekeeper enforcement strategy, i.e., cost-benefit analysis, private enforcement incentives, and comparative merits over alternative methods[10].Processors, like Internet giants, holding a massive amount of personal information, usually proves to be the best candidate for the gatekeeper, in terms of their capabilities to prevent information breach and the cost of disrupting the illegal acts. On the one hand, modern lives are increasingly dependent on the Internet, opening up a"networked lifestyle" in the cyberspace; on the other hand, along with the rapid development of artificial intelligence technology, business organizations' demand for personal information is growing exponentially, in order to more accurately explore the consumers' potential needs and develop successful business models. In contrast, in the face of a wide variety of regulated entities, administrative agencies cannot form uniform regulatory rules for the market brimming with personal information, and a one-size-fits-all approach is challenging to deal with various risks[10]. Additionally, regulators cannot grasp more information than business organizations, thus shifting attention to preventive measures, with less emphasis on result-oriented regulatory details. To a large extent, it leaves the discretion of achieving public management objectives to the regulated entities, using their expertise and judgment to determine the means of achieving regulatory goals and the definition of these goals in a given situation.
2.3 The Criteria of Triggering Discretion in the Breach Notification System
As mentioned above, the traditional reputation sanction system leverages the negative labeling as the core countermeasure to structurally compress the room for discretion, which universally and automatically extends impact of reputation sanction to a wide range of agencies, relevant markets and consumers. However, there is a removal mechanism for the negative labeling, which retains a certain degree of incentive and tolerance. Compared with the removal mechanism of the negative labeling system, breach notification exerts irreversible impacts on processors in that the memory of the network cannot be erased, and the possibility of restoring the social reputation is slim.Therefore, taking into account the severity and irreparability of reputation sanctions, Article 57(2) of PIPL sets up an exemption rule, entitling personal information processors the freedom to "not notify" under certain conditions. In contrast, Article 34(3) of GDPR provides three conditions for exemption, i.e., encryption rule, high risk "no longer likely to materialize" and disproportionate effort involved.
As a trigger for discretion, the "effective" boundary in Article 57(2) of PIPL ("effectively avoid harm caused by information leakage, tampering, or loss") could only be gradually discovered in the process of interaction between the administration and regulated entities, i.e., regulators use the information disclosed by processors to gain knowledge and provide objective criteria for measuring the "effective" boundary. This also applies to Article 34(3)(b) of GDPR (high risk "no longer likely to materialize").
However, Article 57(2) of PIPL provides such a standard that requires a long period of practice to discover as a trigger for the discretion of personal information processors is tantamount to hollowing out their notification liability under public law. Even if the standard of "measures … can effectively avoid harm" can be accurately recognized by public authorities, the harm caused by information breach is still unknown and cannot be objectively recognized.The information breached usually flows into the underground market, i.e., the dark web, where it is bought and sold and then used for other purposes, such as financial credit collection and marketing. This means there is a time lag between the information breach and the occurrence of actual harm. During this time, the damage caused by information breach is unknown and cannot be objectively assessed and measured. Therefore, the breach notification system must set discretionary trigger conditions with operability.
3 Structurally Controlled Breach Notification System
Regarding discretion regulation, Kenneth Culp Davis proposed the concept of "structuring discretion", which aims at controlling the manner of exercising the discretionary power within the boundaries, to produce order and achieve a high quality of justice[11]. Further, the core of "structuring discretion" is how to rationalize and justify the decision through the proper arrangement of procedures. Thus, it is critical to highlight the role of regulated entities as competitors or restraint against arbitrariness. Such a competitive structure allows public authorities and private entities to participate equally in decision-making. Moreover, there are mainly three mechanisms to guarantee the equal participation of public authorities and private entities: first, full information disclosure; second, the right to private entities to make statements, plead and rebut; third, the administration must give sufficient reasons for the decision contemporaneously. Although the discretion of breach notification delegated to personal information processors is based on the public law liability, which differs from the "structuring discretion" in terms of the subject of the right, both of them share a common problem in the exercise of discretion: how to make the exercise of discretion more fair, reasonable, and able to withstand the public's challenge, and thus solve the arbitrariness issue?
Personal information processors have unique advantages in judging whether their remedial measures are "effective" in avoiding the harm of information breach, as processors possess the basic hardware facilities, database systems, and institutional arrangements of operation and maintenance personnel. The introduction of "structuring discretion" proves to be a promising way to improve the breach notification system. Since private entities are delegated the discretionary power, the mechanism to guarantee equal participation of both parties primarily focuses on information disclosure. This paper intends to refine and improve the breach notification system in three aspects (Figure 1.): regular supervision on discretion, weakening clear regulatory indicators, and the effectiveness of notification content.
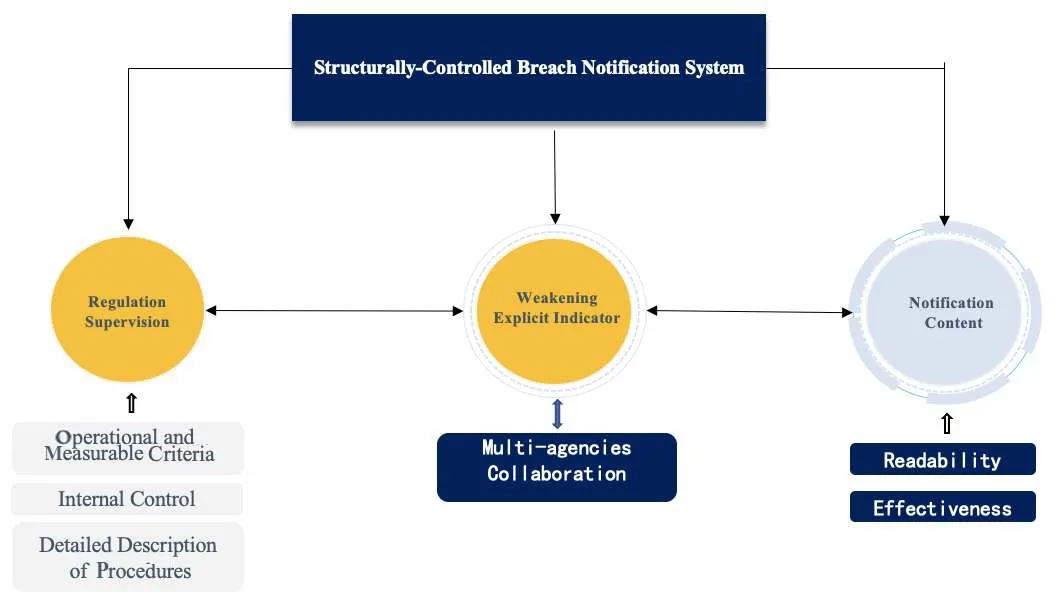
Figure 1 The Structurally-Controlled Breach Notification System
3.1 Regular Supervision on Discretion
First, the discretion under regular supervision should be based on operational and measurable criteria. For example,the Interagency Guidance on Response Programissued by four agencies in the U.S. (i.e., Office of the Comptroller of the Currency, Board of Governors of the Federal Reserve System, Federal Deposit Insurance Corporation,and Office of Thrift Supervision) stipulates that the notification of the affected customers shall be activated "if the institution determines that the misuse of its information about a customer has occurred or is reasonably possible"[12].The triggering criteria of "likelihood of misuse" could be exemplified by the financial system: there must be some fraudulent activities, like opening fraudulent accounts, involving breached personal information. Under the trigger of"likelihood of misuse", it could be far more practical and operable criteria for financial institutions.
Secondly, regular supervision requires continuous involvement in the review of the discretion of personal information processors. Confronting the conflict between administrative regulation and corporate goals, a company's established practices and mindset prompt it to make adjustments in the easiest way to achieve "superficial" compliance while minimizing the externalities associated with compliance adjustments[13].The adjustments made by regulated entities appear to prioritize complying with regulation but in reality, do little to change their internal ways of working. Therefore, the regulator needs to intervene permanently in the discretionary decision process, so permanently those enterprises know that the administrative authority is constantly monitoring and will critically review the decisions regarding breach notification. The standing intervention approach could draw on Sections 302 and 404 ofthe Sarbanes-Oxley Actregarding the provision of internal control, reporting, and deficiencies in annual reports of listed companies, respectively[14].Personal information processors should provide a detailed description of the procedures involved in exercising discretionary decisions, the allocation of personnel responsibilities, and the risk of misjudgment that may result, and report to the administration regularly. In addition, personal information processors also need to elaborate in detail why they make different decisions on similar information breaches in separate cycles,which forces processors to make reasonable and well-evaluated decisions instead of formal compliance.
3.2 Breaking the Regulatory Capture: Weakening Explicit Regulatory Indicators
Traditional regulatory capture usually refers to the phenomenon that organized groups successfully act to defend their interests through government policy at the expense of public interests[15].As to the breach notification system, enterprises gradually learn how to meet specific regulatory requirements and incorporate routine information into their daily compliance process, which may lead to the decision not to notify affected individuals and vindicate their reputation interest at the expense of the public interest[6].
After making a decision at the discretion of processors and choosing not to notify individuals, processors shall report the internal procedures and relevant factors involved in the decision-making and provide it to the administration for ex-post review. Due to the diverse regulated entities, the expertise involved in reviewing the decisions of numerous enterprises is often beyond the capacity of a single administrative agency.
Therefore, it is recommended that the administration shares the decisions from processors with other relevant agencies, collaborates on the review of findings, and weakens the explicit regulatory indicators. In other words, the multi-agencies collaborative review makes it impossible for personal information processors to figure out the regulatory tendencies in the process of regulatory interaction. Especially considering the need to articulate and explain to the authority the relevant internal procedures and potential risk assessments involved in the decision-making process, processors will consider bilateral arguments and evidence to be prepared for the criticism from all sides.Weakening external regulatory indicators will encourage corporate management to reduce reliance on established"knowledge structures", making them more willing to improve and upgrade systems for protecting personal information in response to changing social conditions.
3.3 Effectiveness of Notification Content
Both Article 57 of PIPL and Article 34 of GDPR require the communication of personal information(data)breaches to the affected individual and provide the specific notification content. However, such a communication task delegated to personal information processors or controllers might inadvertently contribute to the boom of phishing, which refers to a kind of identity theft falsely disguising as legitimate processors to an entice individuals to surrender sensitive personal information, like financial accounts or medical recording[16].
Additionally, whether the breach notification is sent by SMS or email, in the era of information, a significant portion of the community will filter the report by spam or junk mail, resulting in a substantial reduction in the system's effectiveness.
Regarding the specific matters to be included in the notification, PIPL and GDPR only stipulate what should be included, but not what should be forbidden. This will lead the business entity that sends the message to take the opportunity to promote sales, etc., and jeopardize the readability of the notification.
To sum up, in terms of the specific content design of notifications and the way to send them, more enterprises and their industries should be allowed to set guidelines and submit them to the regulatory authorities for approval.The initiatives should be encouraged to develop innovative and effective ways to overcome the shortcomings of the existing notifications. Second, the scope of content should be strictly regulated to prohibit any sales promotion that jeopardizes the readability of the notice.
4 Concluding Remarks
With widespread social concern about personal information protection, the refinement and improvement of the breach notification system have become critical. The discretion delegated to the personal information processor in Article 57 of PIPL predominantly affects the effectiveness of the notification mechanism.
The liability of breach notification for personal information processors and the "structuring discretion" proposed by Davis both confront the problem of regulating private entities over-exercising discretion. Given the dominant position of personal information processors in terms of knowledge and information, the procedure to make the exercise of discretion more fairly and reasonably is mainly focused on the aspect of information disclosure. Accordingly, this paper puts forward three suggestions: first, establishing operational and measurable criteria for triggering discretion and continuously intervening in the review of decisions made by personal information processors or controllers; second, weakening clear regulatory indicators, and reviewing the decisions from processors or controllers in a coordinated manner; third, formulating industry guidelines to strictly regulate the scope of content that can be included in breach notification, and improving the readability of reports.
As to the future work on the breach notification system, it is proper to consider behavioral findings on decision-making, such as the heuristics and cognitive biases[17],which might provide novel insights into the policy regarding the notification content.

